Companies have eventually stopped wondering whether it’s safe to move data to the cloud. They simply do it, and now more confidently than ever before. But security still remains a problem that can’t let businesses breathe confidently in the cloud like fish underwater. Nevertheless, despite risks and challenges, cloud computing is the safest place to store data and here is why:
“Cloud computing is often far more secure than traditional computing, because companies like Google and Amazon can attract and retain cyber-security personnel of a higher quality than many governmental agencies.” – says Vivek Kundra, former federal CIO of the United States.
Cloud computing solutions come in three different models: Software as a Service, Platform as a Service and Infrastructure as a Service. We’ll write more on each of them in one of the following articles. What matters now is that each model comes with its risks and requires well-considered actions – no business processes come without risks, especially when they are related to data. Yet it’s possible to prevent them by raising your awareness of all the possible threats and taking all the necessary steps to feel safe in the cloud.
How to Detect and Mitigate Cloud Computing Risks?

We’ve collected a number of major cloud security concerns and your recommended actions to eliminate them.
1). Security breach
This is probably the most serious concern users have about the cloud. When relevant precautions aren’t taken, business data becomes vulnerable to hacking and further malicious use. As a result, sensitive information such as credit card details, personal files or company files can get into the wrong hands. You might already know the outcomes of such breaches. The more massive it is, the more dreadful and painful it is for your business to fix. When access to the cloud has been broken at one point, the attacker gains control over the data at multiple points.
Preventative Steps:
Don’t share account credentials with anyone in the company, even if you trust them. Make sure your software uses two-factor authentication. It’s also necessary to apply end-to-end data encryption. For enhanced security, your data should be encrypted with the help of the SSL/TLS protocol before the upload, while it’s stored in the cloud and when transmitted. Still having concerns about your data safety? Ask an expert to perform vulnerability tests and make sure your software is compliant with security standards.
2). Permanent Data Loss
Either accidentally or on purpose, users can delete data stored in the cloud. Disgruntled ex-employees, inexperienced careless users or simply malicious intruders can remove important data from the cloud storage without any chance to recover it. As cloud computing is a new invention, there still exists a knowledge gap in understanding how to use it properly.
Preventative Steps:
For any piece of information that is valuable for your company, create regular backups and store them securely. Provide different users with different access levels. Modern cloud providers give you a chance to change access settings and enable users to operate only with the data they are eligible to obtain. Third-party audits are also very helpful in identifying any violation coming from inside. Companies should regularly educate their staff about the potential threats and appropriate behavior in the cloud. And finally, human resources personnel should be able to ask the right questions when hiring people.
3). Malware in the cloud
Attempted attacks through deploying malware in the cloud are quite frequent and their success depends solely on your readiness to face them.
Preventative Steps:
Cloud providers should be able to detect any malicious software inside their servers. Ideally, it doesn’t affect the customers in any way and lets them keep using the cloud service without interruption.
Read Also: 8 Simple Steps To Improve Data Quality and Enhance Sales
4). Shared technology
Whenever you use the cloud, you actually share your platform with other users in a virtual environment. By sharing storage, applications or API’s in the cloud, you are subjected to security vulnerabilities.
Preventative Steps:
Keeping your passwords safe is usually not enough. Encrypting data and performing constant security checks are going to be much more helpful in this case.
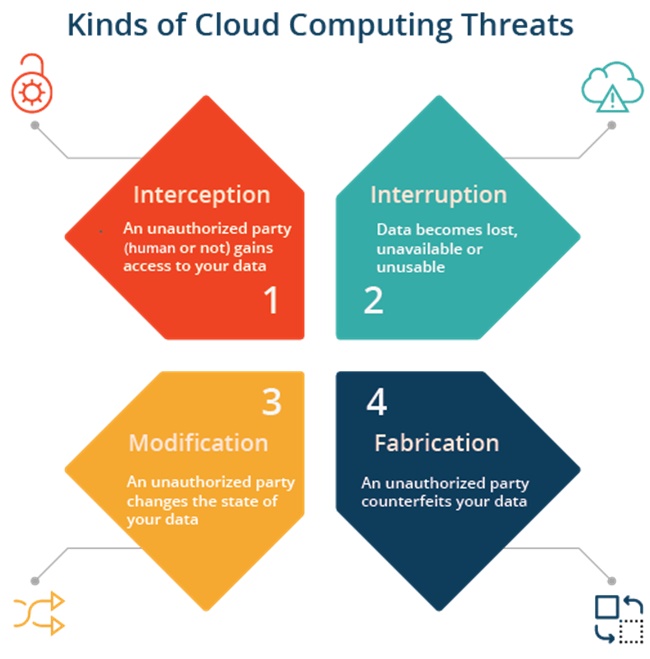
It’s natural for users to expect ultimate data safety from a cloud provider and cloud storage providers have become better in dealing with hacking attacks. They have also become flexible enough to offer this flexibility to their customers who can successfully manage access options for different user groups and manage their accounts more efficiently.
You May Like to Read: Mission Impossible – Organizing Company Files
As Nat Robinson once said: “Cloud providers can’t afford for customers to lose confidence in their service, and therefore leverage the latest and greatest security features to maintain the full integrity of information at all times.”
The question you probably want to ask the most is
Are You Safe in the Cloud?
With the growth of technology, hacking capabilities have risen as well and we should never think that intruders will target only big fish businesses. The statistics are incontrovertible: over 80% of companies faced a security breach because they had a general security weakness rather than being specifically targeted. It means that you have a very small chance of experiencing security problems if you take all the preventative steps to protect your data. Still concerned? We want to know your fears, so you are welcome to comment and share your thoughts.
Author Bio

Beata GREEN is Director of HeadChannel Ltd., London based bespoke software development company. She is responsible for overall strategic direction and overseeing the company’s continuing growth, building closer client relationships and maintaining best working practices. She enjoys brisk country walks with her red fox labrador and then relaxing in front of a TV crime drama with a glass of red wine.